Like many other industries, the legal sector has increased its reliance on technology in recent years. Law companies store and process a huge quantity of sensitive information, from case management systems to electronic document storage. The risk of cyber threats is rising along with our greater reliance on technology. Due to the important and private information they hold, law firms are popular targets for cyber assaults. Thus, suitable precautions should be taken to protect the legal business. This most likely starts with custom software development practice.
Some of the essential tips include the use of secure, one-of-a-kind passwords for all accounts and systems. Complex passwords should contain a mix of characters, numbers, and symbols. Update passwords frequently and stay away from using information that can be easily guessed, including names or dates.
In this post, we’ll look at the cyber risks that law firms must deal with and talk about the best defenses against them.
Cybersecurity tips in the Legal Sector: A quick look
- Implement two-factor authentication (2FA) whenever it is practical for all accounts and systems. Asking users to give a second form of verification in addition to their password, such as a special code texted to their mobile device, offers an additional layer of protection.
- Encrypt sensitive data both in transit and at rest by using data encryption. Encryption methods can be used to safeguard private data from unauthorized access and make sure that only authorized users can decode and access the data.
- Establish a routine backup mechanism to guarantee that important data is consistently backed up and kept safely. This reduces the possibility of data loss because of device malfunction, cyberattacks, or other unforeseen circumstances.
- Employee Education and Awareness: Hold routine security awareness training sessions for all staff members to inform them of potential security dangers including phishing scams and social engineering. Encourage them to immediately report any questionable activity.
- Implement stringent practices during Legal software development like access controls to restrict employee access to sensitive data. Give access to only the required information and systems by allocating permissions by job roles and responsibilities.
Recognizing the Particular Cyber Threats Facing Law Firms
Law firms differ from other businesses in that they are subject to several cyber dangers. The theft of client information is one of the main concerns. Law companies are prime targets for hackers because they retain a variety of financial and personal data about their clients. Various nefarious uses of this information are possible, including financial fraud and identity theft.
The potential interruption of services is a serious concern to law firms. Important data loss from cyberattacks might prevent a firm from accessing case files or connecting with clients. Significant financial and reputational harm may result from this.
In addition, intellectual property theft frequently targets law firms. Numerous organizations have significant trade secrets or confidential information and handle high-profile cases. Cybercriminals may try to steal this data to profit financially or acquire an edge over rivals.
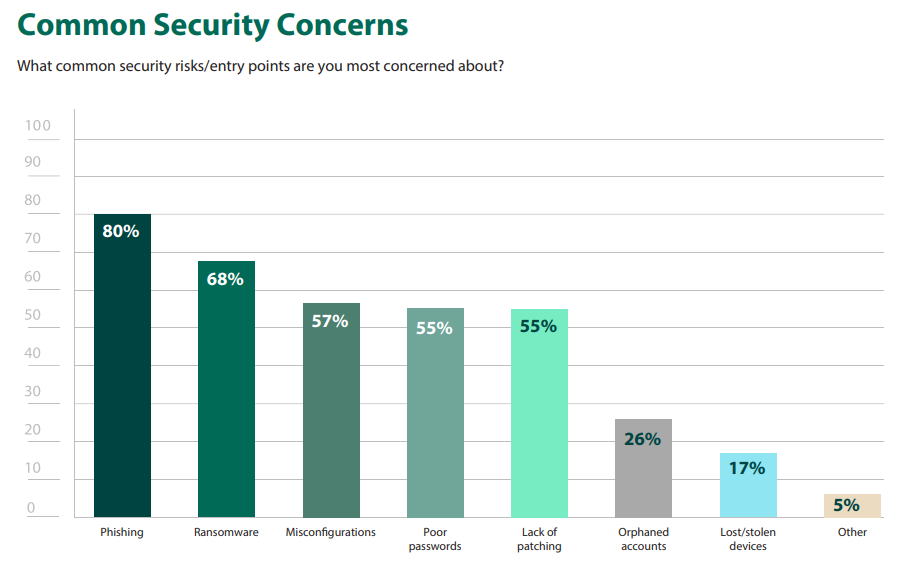
A Law Firm’s Cyberattacks Repercussions
A cyber-attack on a legal practice might have serious and far-reaching repercussions. A company may experience long-term reputational harm in addition to the immediate financial costs of repair and recovery. Clients trust legal firms to safeguard their private information, and a betrayal of that confidence may have long-lasting repercussions.
A cyber-attack may also have legal and regulatory ramifications. Law firms are required by law to preserve client information and to abide by several privacy and security laws. Inadequate client information security can lead to penalties, legal action, and possibly the loss of professional licenses.
A cyber-attack may occasionally result in the loss of customers. Clients might look for legal services elsewhere if a firm’s reputation is damaged because of a data breach, which would result in lost revenue.
Top Cybersecurity Techniques for Law Companies
Despite the growing sophistication of cyber threats, there are several defense mechanisms that law firms can use to counter these assaults.
Putting in Place a Robust Password Policy
Protecting sensitive information requires a strong password policy. The usage of strong, frequently updated passwords should be mandated by law firms. Uppercase and lowercase letters, numbers, and special characters should all be used in your passwords. Multi-factor authentication should also be used as an additional security measure.
Employee Cyber Security Best Practices Training
Employees are essential to keeping cyber security up to date. Employees at law firms should receive frequent training on the value of cyber security and best practices for safeguarding confidential information. Topics including spotting phishing emails, avoiding dubious websites, and using safe Wi-Fi networks should be covered in this training.
Software Patching and Updates regularly
Law businesses may be more vulnerable to cyberattacks if their software is outdated. Hackers frequently use software flaws to get unauthorized access to systems. To guarantee that the most recent security fixes are adopted, law firms should create a procedure for routinely updating and patching software.
Using Access Controls and Encryption to Secure Client Data
Protecting sensitive information begins with encrypting client data. Data can’t be read without the decryption key even if it is intercepted thanks to encryption. To restrict who has access to client data, law firms should create access controls. Access to sensitive information should only be granted to authorized individuals.
Regular security audits and risk evaluations
Finding vulnerabilities and weak points in a legal firm’s cyber security procedures requires regular security audits and risk assessments. These evaluations must be carried out by internal or outside specialists who can offer a dispassionate appraisal of the firm’s security stance. These assessments’ findings can be used to make the necessary corrections.
The Function of Cyber Insurance in Safeguarding Law Offices
Law companies want to think about buying cyber insurance in addition to putting effective cyber security measures in place. Financial security is offered by cyber insurance in the case of a cyberattack or data breach. It can pay for expenses including court costs, data recovery, and notifying affected parties. Business disruption and reputational harm are two more coverage options for cyber insurance.
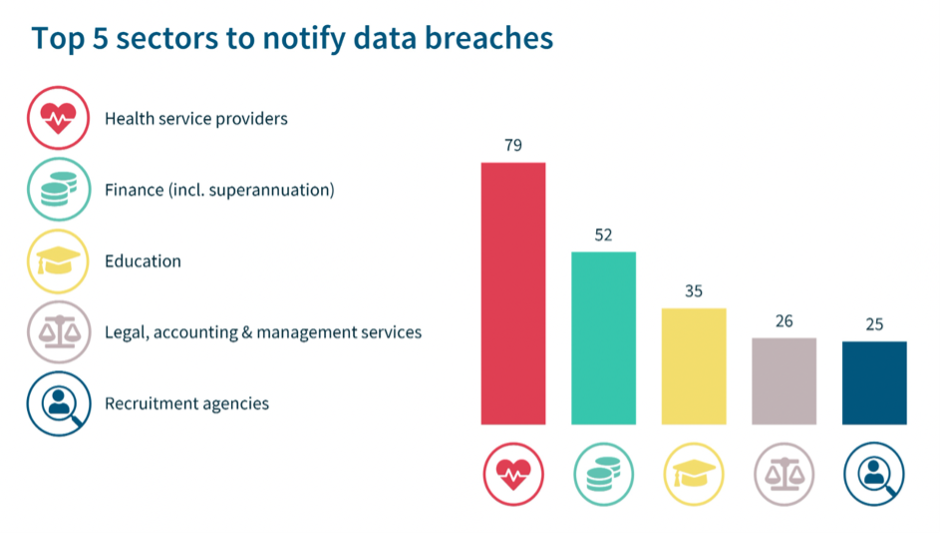
Even if strong cyber security measures should always be used, cyber insurance can add another layer of security and lessen the financial effect of an attack.
Cybersecurity Best Practices for Legal Industry Remote Work
Law companies must consider the distinct cyber security challenges that come with this new mode of working as remote work becomes more prevalent. As they frequently utilize personal devices and networks that might not have the same level of protection as office systems, remote workers may be more susceptible to cyber-attacks.
Law companies should make sure that remote workers have access to virtual private networks (VPNs) and secure devices to encrypt their internet connections. To prevent unwanted access to systems, it is also important to install strong authentication techniques like biometric or token-based authentication.
Additionally, recommendations on how to handle and send client information securely should be given, as well as training on the specific cyber security threats connected to remote work.
Plans for incident response and recovery are crucial
Even with the finest security measures in place, law firms must be ready for a potential cyber-attack. Plans for incident response and recovery include instructions on what to do in the case of a breach and help to lessen the effects on the company and its clients. These strategies must include procedures for promptly locating and containing a breach, notifying those who might be impacted, and regaining access to systems and data.
The effectiveness of these programs must be regularly checked and updated. To evaluate the responsiveness and recovery capability of their incident response plans, law firms should carry out simulated breach exercises.
Collaborating with IT experts and cyber security professionals
Even while legal companies might have internal IT departments, working with outside cybersecurity specialists can offer insightful advice and experience. Law companies may stay current with the most recent risks and best practices by working with specialists in the field of cyber security, which is an area that is continually expanding.
Comprehensive security audits, assistance in creating and implementing successful cyber security plans, and ongoing monitoring and support can all be provided by external experts.
Conclusion
To safeguard their clients’ confidence and sensitive data in the modern digital era, law firms must implement strong cyber security procedures. The first stage in preventing cyber assaults is to have a thorough understanding of the cyber dangers that the legal sector faces. The second step is to put these methods into practice, including strong password policies, personnel training, frequent software upgrades, encryption, and access controls.
Additionally, law firms ought to think about purchasing cyber insurance to offer financial security in the event of a breach. Additionally, with the increase in remote work, it is crucial to develop specific cybersecurity measures for remote workers.
Law companies can remain ahead of the constantly changing threat landscape and guarantee the continuing protection of their priceless data by cooperating with IT professionals and cyber security experts.








+ There are no comments
Add yours